On July 12, Oki Electric Industry Co. Ltd. (OKI) and Professor Shingo Ata of the Graduate School of Informatics at Osaka Metropolitan University announced that they have developed a technology to detect unauthorized network intrusions in real time, such as an unauthorized connection to IoT devices and malware infection, based on their multi-year 'joint research on communication traffic analysis.'
This technology can automate IoT device management and enable the early detection of abnormal device communication due to spoofing or malware infection as an unauthorized intrusion that could lead to information leakage.
In the field of network security, the 'zero trust' strategy, in which even the devices inside a network are considered untrustworthy, has become essential owing to the increasing number of internal infections caused by targeted attacks and unauthorized intrusions into an organization's network by exploiting vulnerabilities in virtual private network (VPN) devices. In addition, even in non-Internet environments, such as equipment networks in factories, which were considered safe, the use of IoT devices and communication with external networks have expanded, resulting in cyberattacks that use poorly managed IoT devices as intrusion points.
These circumstances make it difficult to detect unauthorized intrusion from outside a network using only perimeter security measures such as conventional firewalls, and security measures at each location (edge area) of an organization's network are becoming increasingly important.
Provided by Osaka Metropolitan University
OKI and Osaka Metropolitan University have long been engaged in joint research on traffic analysis technology that passively observes and analyzes the traffic of IP communication devices and estimates their state. As a result of this cooperation, they have developed a technology that can determine if the connection of IoT devices is unauthorized or not in real time while acquiring the communication characteristics of the devices in a timely manner.
By using this technology and learning approximately nine types of traffic data of four models acquired from the core network of the Sugimoto Campus of Osaka Metropolitan University, they evaluated whether IoT devices can be identified in real time from the characteristics of communication traffic. Consequently, a demonstration experiment in January 2023 confirmed that IoT devices can be identified with a high accuracy of 97.7% as soon as they are connected to a network.
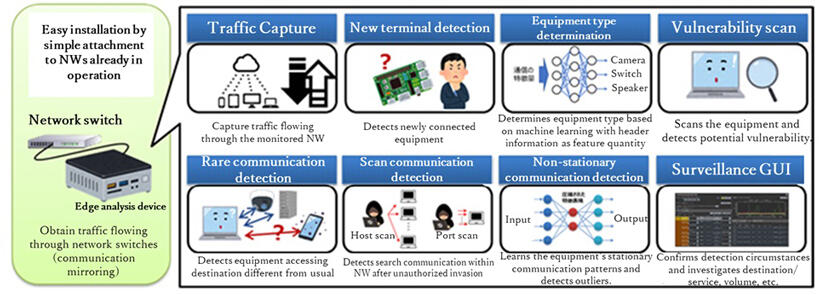
Additionally, OKI has developed a 'real-time network monitoring system' equipped with a communication non-routine detection function that detects deviations in normal communication behavior, a vulnerability scan function that detects improperly configured devices in the network and easy ID/password detection, and a monitoring graphical user interface (GUI) that visualizes device connections and communication traffic in the network and notifies administrators. The system can visualize the connection configuration and communication status within a network and automatically extract suspicious or risky devices.
In addition, these functions are provided in a compact and lightweight stand-alone device, which can be easily retrofitted and installed in an existing network by simply connecting it to a mirror port on a network switch.
This system is currently implemented in several of OKI's production plants, and OKI continues to improve the system while obtaining feedback from on-site network administrators. The system is also suitable for monitoring offshore sites where it is difficult to thoroughly enforce security policies and networks operating legacy equipment in which installing security software is difficult.
OKI is looking for partners for conducting verification experiments by manufacturing verification machines that can be provided immediately, to increase the number of verification cases in various user environments for early commercialization.
This article has been translated by JST with permission from The Science News Ltd. (https://sci-news.co.jp/). Unauthorized reproduction of the article and photographs is prohibited.




